
https://i.kym-cdn.com/entries/icons/mobile/000/026/380/lock.jpg
What is Ethical Hacking?
Ethical hacking is a specialized cybersecurity practice that focuses on assessing the security of infrastructures and applications from an authorized and controlled perspective. Depending on the security professional consulted, it may also be referred to as “penetration testing” or “pentest.” For the purposes of this article, these terms will be considered interchangeable, representing a different type of analysis with varying methodologies and scopes.
If you’re interested in learning more about these tests, we invite you to read our article All About Penetration Testing (Pentesting), where we explore the benefits, phases, and how they help strengthen cybersecurity.
In contrast to malicious hackers, ethical hackers use their skills to identify and address vulnerabilities rather than exploit them for malicious purposes.
Who Might Want to Target Me?
It’s a common belief that if you haven’t experienced (or detected) an attack, no one would be interested enough in your organization or application to target it. However, various actors may have your organization in their sights, even if it’s through automated processes like scanning the entire internet.

https://images.pexels.com/photos/6963944/pexels-photo-6963944.jpeg
“Opportunistic” attackers may identify at least one vulnerability in multiple targets and attempt to exploit it, usually on a massive scale. If successful, they assess how much they can benefit from the advantage and the available accesses. A similar category, but with less knowledge, includes “script kiddies,” who use automated analysis tools without fully understanding their functioning or the potential damage, simply focused on obtaining an easy result.
Another type of threat agent is the motivated hacker, whether by contract or another form of motivation sufficient to select specific targets. These individuals have advanced knowledge, time, and dedication, usually following a methodological approach.
Then there are more advanced groups, such as hackers from criminal organizations and/or government-sponsored entities. An application or organization may be the ultimate target, or it could be an intermediate target used as a tool for a larger attack (as with botnets).
Any of these hacker types, which can be categorized in other ways, are potential attackers to consider.
Types of Ethical Hacking
One way to classify types of ethical hacking is based on the variants of threat agents considered in a preliminary analysis, ideally a proper threat modeling.
If we consider the aforementioned classification, a valid approach is to focus on external accesses with perimeter analysis of the organization or application. This approach is usually done anonymously, without access credentials, and with no information about the target except an access point (URL or IP address). In this context, it is referred to as “black-box” ethical hacking, associating it with the concept of “opaque” due to the lack of knowledge about the internal workings.
When the focus extends beyond external accesses, minimal access to the application or organization is provided. In the specific case of applications, access credentials are provided with at least one user role or profile to explore functionalities and attempt to abuse access controls to privileged functions or data, either with users having the same role (horizontal escalation) or with a role of higher permissions (vertical escalation). This approach of partial access and knowledge is called “gray-box.”
Finally, if there is complete access to documentation, credentials, and, in the case of applications, the source code, there is knowledge to conduct a thorough analysis known as “white-box.” Such an analysis allows the ethical hacker to discover vulnerabilities based on lack of knowledge (security through obscurity) or simply assess security in terms of an individual internal to the organization or application.
In ethical hacking endeavors, time is a scarce resource as it involves a service contracted to third parties or dedicated internally, but with a defined scope. It’s relevant to consider that white-box or gray-box analyses save testing time since there is inherent visibility that allows discarding if a control is vulnerable.
Compared to black-box analysis, the latter generally attempts verifications with a broad set of tests to achieve detection or exploitation. The test set is reducible with experience and other circumstances associated with the nature of the analyzed target.
Ethical Hacking Tools
The toolkit of an ethical hacker is diverse, depending on whether the target is an infrastructure or an application; the tools necessarily differ. Frameworks like Metasploit concentrate modules for detection and exploitation of multi-purpose vulnerabilities. There are also Linux distributions like Kali and Parrot OS containing tools for all types of security analysis.

https://images.unsplash.com/photo-1426927308491-6380b6a9936f
Analyzing infrastructures commonly involves using scanners like Greenbone or Tenable/Nessus, to name a few. Some hackers build their toolchains and automations with open-source tools to avoid commercial products. Nmap is another popular tool for port scanning and executing validation or exploitation scripts when a potential vulnerability is detected. If access to the infrastructure is obtained, the choice of additional tools depends on the present technologies.
Regarding application analysis, some of the mentioned tools apply, but direct human interaction with attack proxies is the usual approach since it’s necessary to analyze the logic flows of the application in depth. An attack proxy is an application that acts as an intermediary between clients (browsers, mobile applications) and servers, allowing visualization and manipulation of traffic in both directions. Examples of these products are Zed Attack Proxy (ZAP, formerly part of the OWASP foundation) and Burp Suite.
The following image shows a sample view of Burp Suite with a history of interactions between a browser and an application in tabular form. With a selected row representing a request-response interaction, messages in raw format can be viewed:
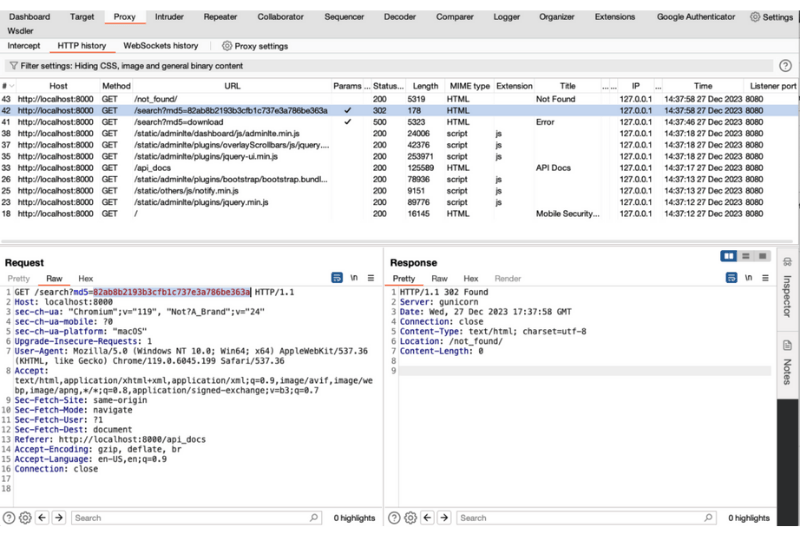
An ethical hacker analyzes all the components that make up this interaction to identify entry points to the application and attempt abuse through the means they find suitable.
Similar to infrastructure analysis, in an application with specific technology, suitable tools will be used. For example, a WordPress site would be analyzed with the WPScan tool.
Best Practices for Ethical Hacking
For both parties in the analysis agreement, it is advisable, and in some cases necessary, to adhere to guidelines or practices that ensure a quality service. Below are some, not exhaustive, given that each situation requires different elements.
Prior to starting the work, there should be at least a confidentiality or non-disclosure agreement. It is advisable to have a well-defined scope, whether granular by application, set of functionalities, list of domain names, or IP addresses, among others. It must be ensured that the client has authorization power to enable the analysis on the selected target(s).
During execution, it is recommended for the analyst to follow a methodology, whether standard or customized, to maintain replicable order. Also, documenting the evidence of the process and keeping a history of actions, either manually or through the tools used, is essential. It is crucial to respect the integrity and availability of the analysis target, especially if it is a system in production. If there is a risk of affecting any of these factors, it is advisable to communicate with the counterpart to request authorization to proceed.
Upon completion, it is important to provide evidence of the findings that is understandable for each recipient in their role. For example, having an executive summary section that is less technical for managerial profiles or those with less technical knowledge, and then a more detailed one with evidence in reproducible steps (variable depending on the profiles involved on the counterpart side).
Finally, it is recommended for the analyst to discard the work environment, and for the client to clean up records resulting from the analysis, such as users and other data. Also, having a validation meeting for the findings is important for everyone to be aligned with the understanding of the report.
Importance and Benefits of Ethical Hacking in Organizations
Ethical hacking is an essential practice for companies of all sizes. In a world with accelerated digitization due to the 2020 pandemic, businesses are exposed to a wide range of cybersecurity risks.

https://images.unsplash.com/photo-1578930955087-58a5d98e7a95
In conclusion, ethical hacking helps organizations identify and mitigate these vulnerabilities, resulting in the following benefits:
- Continuous Security Improvement: By discovering and addressing vulnerabilities, ethical hacking contributes to strengthening an organization’s defenses, implementing controls at the software, hardware, configuration, policy, education, and other levels.
- Regulatory Compliance: Many industries and organizations are subject to strict regulations regarding data protection. Ethical hacking helps ensure regulatory compliance by identifying and addressing potential security gaps.
- Reputation Protection: Avoiding cyber attacks helps preserve a company’s reputation, as customer and business partner trust remains intact.
- Enhanced Security Awareness: By simulating real attack scenarios, ethical hacking helps companies be prepared to face potential threats and develop effective responses. Demonstrating impact in reports is essential to generate awareness of what is possible to achieve and the potential associated damage.
- Cost Reduction: Ethical hacking can help companies reduce cybersecurity costs by identifying and addressing security vulnerabilities before they are exploited by attackers.
While a one-time offensive perspective service like a penetration test is beneficial in many aspects, it is not the only type. It can be executed with a penetration scope where the analyst does not stop at exploiting a vulnerability but advances as much as possible without necessarily assessing other risks present in the initially analyzed target (classified in this article as penetration testing).
Each type of analysis has its benefits and shortcomings. There is also a defensive approach where security is internally evaluated without the need for evidenced attacks. Organizations must be able to assess which types of analysis fit their realities and needs, considering it as an ongoing task, as evolution and maintenance are continuous.
Finally, it is worth highlighting that ethical hacking is one of many measures to take in technological construction and evolution. Security is manageable with various activities at all stages of development life cycles for applications or the assembly and maintenance of infrastructures, a game that never ends.




